
Twitter has become the battleground for the 2012 elections and the fight to push the country further left or closer to the right. It is the vehicle that not only informs and influences the opinions of others, but often it is Twitter that actually drives the news cycle. Protest movements like Occupy and Anonymous are using Twitter and other online media as a key mechanism in fighting the battle for ideas and opinions.However, for months now, there has been a coordinated campaign on the part of some leftists to silence conservatives on Twitter in an effort to reduce the impact of the right’s voice on public opinion and the news.
It’s a campaign that has been obvious to many of those who’ve been experiencing this first-hand. And Sunday night, more sunlight was shone on the issue as thousands witnessed an attack on a higher profile target when Chris Loesch, the husband of Big Journalism editor and CNN contributor Dana Loesch, had his Twitter account suspended suddenly and unexpectedly–for “sending multiple unsolicited mentions to other users.”
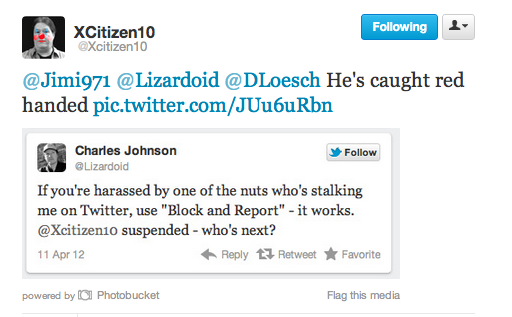
The action sparked an outpouring of support, sending the hashtag #FreeChrisLoesch to the top of the trending tags, and once more with #FreeChrisLoeschAGAIN when his account was suspended yet again (and again) after less than a minute or so of having been restored.In reviewing the tweets that lead up to the incident, there is no evidence whatsoever that Chris abused Twitter’s terms of service. His “infraction” was the mere act of defending his wife by responding to those targeting her with vile, disgraceful tweets, all of which Dana has aptly reported here on Big Journalism.
It was later discovered that the cause of Chris’s suspension stemmed from a coordinated effort to abuse Twitter’s “block and report” features to trigger Twitter’s algorithm that flags an account as spam, thereby automatically suspending the account temporarily until human eyes could review the situation. Many outlets have since covered Sunday night’s incident, including, but not limited to, Human Events, Newsbusters, Twitchy and The Washington Times.The truth is, this isn’t the first time that this has happened to a conservative on Twitter. In fact, many have experienced this and other attacks in recent months. Sunday night was simply the first time that conservatives fought back–en masse.
We’ve all seen tactics like this in action online in one form or another. Over time, countless numbers of activists on the right have sent me examples of similar attacks, and I’ve even spoken directly with many of them. We thought this might be the perfect opportunity to share a list of the “Top Ten Dirty Tricks Leftists Play Online.”
I’ll preface this list with a couple of obvious caveats.
First, I know that there are some on the left who vehemently disagree with such tactics, and to those individuals, I say thank you for standing up for free speech even when it does not reconcile with your own beliefs. I wish more on the left would speak out in support of all free speech.
Secondly, I would venture to guess that there are some on the right who might not play entirely fairly, either. I don’t believe many on the right would excuse that behavior. The observation from many however, is that the instigators of such tactics as I’m about to list below appear to be overwhelmingly left-leaning.
That being said, here is the list, by all means not all inclusive and in no particular order, compiled from examples that have been sent, tweeted, posted and discussed in recent months.
- Google bombing: The act of flooding search engines with intentional disinformation about a person or group in order to mock or harm their reputation. This is usually then extended to Twitter. Even in the days before the infamous Santorum Google bomb, this was already a frequent and universal tactic. Check out some of the most notorious Google bombs here. Often, the best remedy to a Google bomb is a counter-action to flood the search results with the truth.
- Comment trolling: Amongst the midst of legitimate commenters on a site are comment trolls. You know them well–the commenters that say outlandish things to provoke a response, sometimes to provoke YOU into saying something that can be used to make you look bad. As with any moderated website, many of you have seen instances of this here at the Breitbart sites. Sometimes, the comments are even plucked from the boards, often before a moderator has been able to address them, and the comments are tweeted publicly. It’s an issue that any site owner struggles with on a regular basis. A proposed law in Arizona to curtail comment trolls has more recently put this problem on the map, and sparked a major civil liberties debate. Best defense when you spot a comment troll? Rule #14. Or, if you suspect it’s a troll whose comments were made to be tweeted, report them using the moderation feature. And tell others to do the same,
- Doxing: The act of posting one’s personal information online. This is an intimidation tactic that’s become even more popular with the advent of groups like Anonymous, which frequently employ the tactic (at times getting the information wrong), and even celebrities, as we saw when George Zimmerman’s address was retweeted by Roseanne Barr and Spike Lee. Even hackers fear doxing by their own, as the attorney for one high profile member of Anonymous indicated, “The publicly available information may then be used to harass the cooperator and the cooperator’s family in a variety of ways,” she said. “This obviously creates danger for the cooperator, the cooperator’s family, and law enforcement.” Posting publicly available information online is not illegal. Therefore, sometimes the only defense you may have is to report the action to the site hosting the information, assuming the act violates its terms of service. If the information itself was obtained illegally, such as in the case of email hacking, this should be reported to your local law enforcement authorities.
- Submitting false complaints: Opponents will often retaliate against one’s beliefs by sending complaint letters/emails to the employer or to any organization associated with their target. I have seen examples of complaint letters that contain everything from lies about the target being “racist” or “homophobic,” to the extreme of falsely accusing the target of wrong-doing or even of crimes. Given that many activists prefer to keep their politics separate from their careers, this can be devastating to some. If you suspect this could happen to you, it may be best to discuss this privately with your Human Resources department in advance, if you have that luxury. I have seen some instances that amounted to defamation, and the targets eventually sued over the loss of or impact to their jobs as a result. Legal action is not always the best course; however, and the potential for converse effects should be carefully considered and discussed with a legal professional.
- “False Flag Suspensions”: The act of abusing Twitter’s spamblock feature to get accounts suspended. Given the intro to this post, this hardly needs further explanation. However, I will offer yet another example. Keep in mind that some opponents seem to have an interesting view on what constitutes “harassment” or “stalking”–views that don’t necessarily line up with the law enforcement community’s definition of those terms. In other words, some might consider your defending yourself to be “stalking” or “harassment” of them. Luckily, companies like Twitter often disagree, once they have a chance to review the situation.
- “Digital Gangstalking”: The act of multiple accounts pursuing a target online in a coordinated fashion. This is common on Twitter especially, where groups of users will all attack a target at once, often in response to a tweet or tweets that a single user sends out. The goal is to attack in such volume as to make it impossible for the target user to block all of the accounts at once and to frustrate and disorient the target user, again in the hope that s/he will react in a manner that reflects poorly on them. Given that blocking has not been an adequate defense in this instance, some users have turned to using hashtags to signal to followers that an orchestrated attack against them is underway (i.e. “#TeamLC”). Sometimes this is not only for the support, but because it is just as likely, if not more so, that the opponents will be the ones to react in a negative manner. And who wants to miss out on that? Of course, the easiest defense, and possibly a more appropriate one if they’re merely throwing around insults, is to simply step away from the computer for a bit. This is precisely why many choose to retweet their attackers’ tweets–let the haters expose themselves.
- Troll/Sockpuppet accounts: These are accounts that political opponents set up for the sole purpose of harassing targets online. That harassment can be as benign as simply sending annoying tweets to the target, or it might entail falsely accusing the target of crimes or highly offensive behavior, i.e. being a pedophile, hate speech, racism, bigotry, etc. However, such accounts are sometimes deployed for even more sinister purposes, and in a very insidious way. There have been instances when opponents have slowly infiltrated what they perceive to be “cliques” on Twitter, in an effort to break up groups of support and to cause distrust and chaos within the faction or the entire movement. This level of deploying troll/sockpuppet accounts is a type of harassment that is along the lines of what is known as a “psychological operation” (PSYOP), and it is not typically conducted by the casual Twitter user, but by a more organized political operation. It is unfortunate that such activities occur online, but the truth is they do. This level of troll activity is less common than the others, but it does occur when certain opponents (usually part of an organization or group of individuals) feel that their target(s) have enough influence to jeopardize the goals of their group or organization, often a political candidate’s campaign or an issue campaign. Disinformation dissemination and social engineering, which was once reserved for hackers and various types of criminals, is unfortunately now a common component associated with the higher-level harassment seen in some organized political operations–but this is a subject that is much more involved and deserves a post of its own in the near future.
- Parody accounts: The use of accounts created to mock an opponent. These will usually resemble the target’s real handle or name, and are most commonly used as satire. However, many can be more malicious–some may recall the disgraceful account that was created on Twitter to parody the wife of Andrew Breitbart immediately after his passing (and which has since been removed). The best defense is either block and ignore, or simply counter the account with one of your own. Humor can often be a great weapon of defense.
- Changing content and adding target names to tweets/retweets: Opponents will sometimes manually change a target’s tweets to contain offensive content and then send or retweet them in such a way that makes it appear as though it’s coming from the targeted user. Rather than use the “retweet” function on Twitter, they copy and paste a tweet, change the content, and add the “RT” in front of the tweet. Or, they may find a derogatory tweet from another user, then simply add the target’s name and the RT in front of it. Some frequent users of this tactic have also been known to obsessively monitor the target user’s followers, and will then search online to find any of the followers’ derogatory statements, then tweet about the target user’s association to that follower. This is frequently done to break up lines of support and/or to cause conflict with the target’s followers.
- Signing up target users for various services, donations or spam: (donations often include a highly derogatory or offensive comment made to correspond with the donation, i.e. “I made this donation to the KKK because I hate black people.”)
Always remember that the primary goal of any of these tactics is to occupy the target’s time and energy. The more time a target spends on defending her/himself, the less time s/he spends on more productive activities, like blogging about important issues.
Secondary to this is often the goal of discrediting a target in some way. It is important for those of us online not only to recognize the tactics and to expose them; it is just as important to know when fighting the fight becomes counter-productive.
In the end, if you spend too much of your time defending and fighting back, you might just be playing right into the hands of your opponent and giving them exactly what they want–your time. The trick is to learn which battles to fight, and which to let go. Most importantly, learn when and how to reach out for help. #FreeChrisLoesch is a perfect example of a counter-attack executed well.
COMMENTS
Please let us know if you're having issues with commenting.