A digital key buried in the emails sent by Hillary Clinton’s staff shows that many of the most important emails released via Wikileaks have not been modified or falsified, according to a series of tests conducted by security experts and by Breitbart News.
The tests are important because they undermine efforts by Democrats to deter media coverage of the Wikileaks emails with vague claims that the messages cannot be verified, or could be faked, or modified. So far, those claims have been made by Donna Brazile, the interim head of the Democratic National Committee, and by Sen. Tim Kaine, Hillary Clinton’s choice for her vice-president.
On Tuesday, for example, White House spokesman Josh Earnest said Tuesday that “I can’t verify the integrity of these emails,” when he was asked about an email which showed Clinton’s staff knew that President Barack Obama was communicating with Clinton via her secret home-made email system. The email contradicts Obama’s March 2015 claim that he learned about Clinton’s server at “the same time everybody else learned it through news reports.”
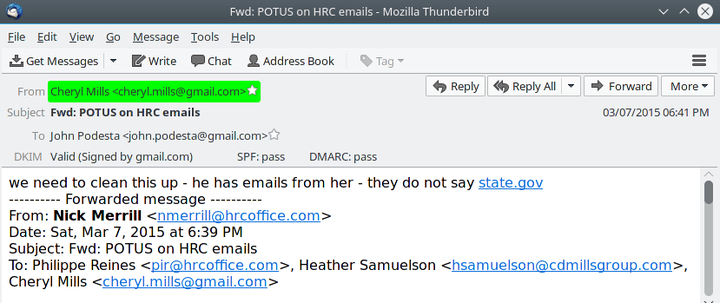
But Breitbart News used commercial software and a basic e-mail verification system to confirm that the Clinton staff email — “he has emails from her — they do not say state.gov” — is valid, true and unmodified.
These Wikileaks emails come from an account used by John Podesta, the chairman of Clinton’s presidential campaign. He has suggested some of the emails are faked, and he has also tried to distract journalists from the revelations by complaining about Russian’s possible role in the hacking.
But each email contains a unique digital key, which is actually a unique number so huge that it is almost impossible to guess, fake, or copy. The key, which is automatically created by the email server at Clinton’s organization, is added to each email as it is first sent, so that if the message is later altered, the key will show other email servers that the original message did not come from the claimed server, or that it has been altered.
The proper name of the process is “DomainKeys Identified Mail,” which is shortened to DKIM.
DomainKeys Identified Mail (DKIM) lets an organization take responsibility for a message that is in transit. The organization is a handler of the message, either as its originator or as an intermediary. Their reputation is the basis for evaluating whether to trust the message for further handling, such as delivery. Technically DKIM provides a method for validating a domain name identity that is associated with a message through cryptographic authentication.
The digital keys in the messages fit into a widely used encryption system that is not controlled by Wikileaks or any other group.
When security experts test the Wikileaks’ email keys against the shared encryption system, they find that the emails are unmodified.
The DKIM key is practically impossible to forge, Robert Graham, a principal at Errata Security told Breitbart News.
Readers can conduct the DKIM tests themselves. For example, the commercial email program Thunderbird allows a “DKIM” add-on, which automatically checks the key in each message against the shared encryption system.
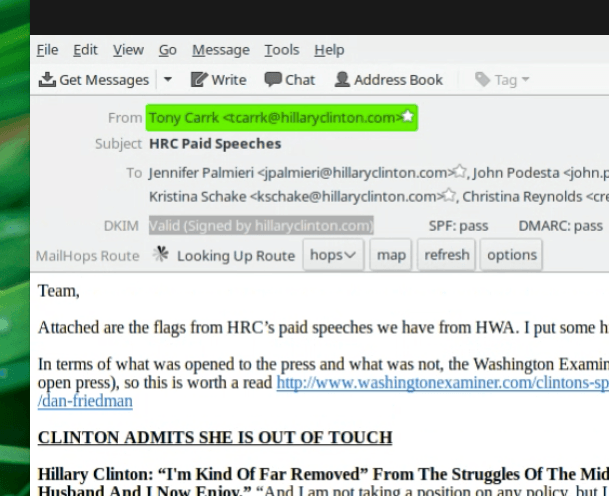
Breitbart, for example, tested the email which contains apparent drafts of Hillary Clinton’s speeches to Goldman Sachs. The email was sent by Clinton staffer Tony Carrk to Podesta. The test showed that Carrk’s DKIM key was correct, and his message — which included the speeches — from Clinton’s server was judged “valid.”
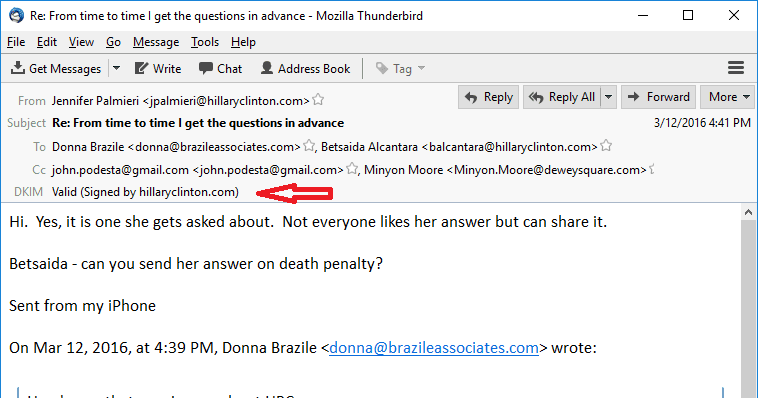
Here is another message validation provided by Graham, which bolsters evidence that Brazile leaked a townhall debate question to Clinton during the primaries.
Security experts have successfully tested many of the messages via different versions of the DKIM process.
Some of the messages failed some DKIM tests but passed also passed other other DKIM tests. Security experts blame the few failures on the process by which Wikileaks’s source may have copied and disseminated the emails. But they warn if a message is validated by even one test, then that message is valid and unchanged.
“There are lots of reasons” why a valid message released via Wikileaks might fail a few DKIM tests, said Graham. For example, the Wikileaks process may drop digits from buried code in the message, he said.
“DKIM is super finicky. If someone at wikileaks accidentally hit tab, or spacebar or whatever and then saved it, that’s enough for DKIM to fail,” said another person checking the emails.
This post on /r/wikileaks brings up that a number of recently released e-mails failed DKIM verification.
I can confirm that the e-mails in this post did fail DKIM verification. (And I thank the user for taking the time to check them and bring it to our attention!) However, there are a number of explanations for this.
This e-mail (25226) is one of the ones that fails DKIM verification.
Fortunately, this e-mail (600) is later in the same e-mail chain. That means everything in e-mail 25226 is included in e-mail 600.
E-mail 600 passes DKIM verification. Therefore, everything in 25226 has been verified by 600.
Multiple Democrats are insisting that the emails released by Wikileaks are untrustworthy because they may have been altered.
When pressed by Megyn Kelly on Fox to explain an email from her account that shows she revealed a question to be asked at a CNN TV-debate, Brazile evaded. “I am not going to try and validate falsified information,” she said.
As a Christian woman, I understand persecution … Your information is totally false … you’re like a thief that wants to bring into the night the things that … I have seen so many doctored emails. I have seen things that come from me at two in the morning that I don’t even send. There are several email addresses that I once used … This has not been verified … This is under investigation.
Similarly, Kaine dismissed the Wikileak messages after the site announced via Twitter it will release a surprise related to Kaine.
“I don’t know whether it was doctored or whether the person sending it didn’t know what they were talking about,” he said Oct. on “Meet The Press” Sunday TV show. “But, clearly, I think there’s a capacity for much of the information in them to be wrong.”
The Wikileaks site subsequently repeated its claim.

COMMENTS
Please let us know if you're having issues with commenting.