On Monday, a Google security researcher announced the discovery of code in the “WannaCry” ransomware virus that suggests a notorious North Korean hacking group is behind the major global cybercrime.
Researcher Neel Mehta revealed the discovery in a puzzling Twitter message:
As security firm Kaspersky explains, the message refers to a block of code found in both an early version of the WannaCry virus – the far less harmful version that was turbocharged into a global menace with the addition of stolen National Security Agency hacking tools – and code obtained from a hacking group called Lazarus in 2015.
In other words, this code snippet is a “fingerprint” that suggests WannaCry was developed by the Lazarus group. Lazarus is associated with North Korea and has a long history of wantonly destructive behavior – most notoriously including the attack on Sony Pictures Entertainment over the movie The Interview, which was seen as insulting to North Korean dictator Kim Jong-un.
“The scale of the Lazarus operations is shocking,” Kaspersky’s Global Research & Analysis Team notes. “The group has been very active since 2011 and was originally disclosed when Novetta published the results of its Operation Blockbuster research. During that research, which we also participated in, hundreds of samples were collected and show that Lazarus is operating a malware factory that produces new samples via multiple independent conveyors.”
Kaspersky’s report considers the possibility that this code is a “false flag,” planted deliberately by other hackers looking to frame Lazarus for the WannaCry attack, but concludes that scenario is “improbable.”
Other possibilities are that Lazarus code was inadvertently copied into the early versions of WannaCry or that Lazarus created WannaCry but was not directly involved in weaponizing it with NSA software and unleashing it on the world last weekend.
However, Kaspersky researchers are confident, based on other forensic details, that the WannaCry code analyzed by Neel Mehta is the precursor to the virus that attacked systems around the world on Friday.
The New York Times reports that U.S. government officials have seen the similarities between WannaCry and the weapons employed in previous cyber attacks linked to North Korea, including the Sony hack, an assault on the central bank of Bangladesh last year, and an attack on Polish banks in February. The NYT notes that this code has only been seen in malware used by hackers linked to North Korea.
“Attribution can be difficult. I don’t want to say we have no clues. But I stand assured that the best and brightest are working on this hack,” Homeland Security Adviser Tom Bossert said on Monday.
Reuters reports that South Korea’s Hauri Labs confirmed the similarity between WannaCry and “North Korea’s backdoor malicious codes,” as senior researcher Simon Choi put it. Choi is highly experienced with North Korean cyber-espionage and is an adviser to South Korean intelligence and law enforcement agencies.
Reuters notes that the Chinese Foreign Ministry had no comment on the record about North Korea’s possible involvement in the attack, which has done considerable damage in Asian countries, including China.
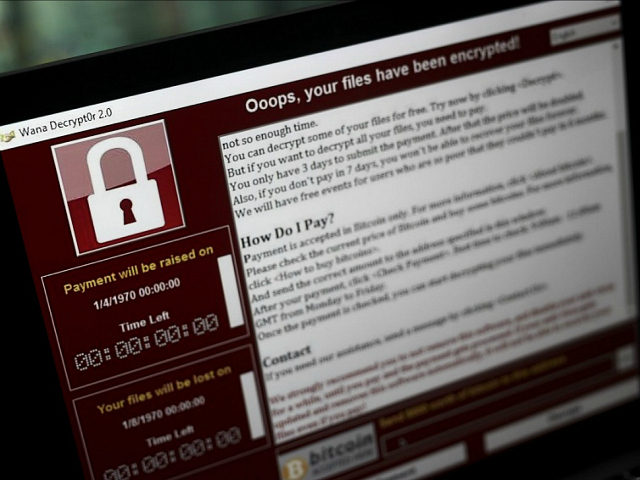
All researchers and officials quoted on the possible North Korean link point out that the evidence is not “smoking gun” conclusive. Also, there are questions about whether the WannaCry attack is consistent with the strategy employed by North Korean-aligned hacker gangs. They have been interested in stealing large sums of money in the past and have used Bitcoin to collect ransoms, as WannaCry does, but they also tend to be more careful about collecting payments.
WannaCry has been characterized as a sloppy attack with poor money handling on the ransom end, putting an almost absurdly small sum in the hackers’ Bitcoin account compared to the scale of global havoc they have inflicted. High-end estimates of the hackers’ take say they collected less than $70,000 by Monday afternoon, although Bitcoin experts say the actual profits could be even lower because some of the transactions hitting the criminals’ Bitcoin account appear to be test transactions and fluctuations in the notoriously volatile Bitcoin currency must be considered.
That is a paltry amount of profit given that a ransomware attack of this magnitude could have been expected to pull in at least $60 million for the crooks, and risk-modeling analysts believe the costs from the attack could reach $4 billion worldwide. That would be a remarkable degree of ineptitude from the same crew that stole $81 million from the central bank of Bangladesh, allegedly to feed isolated North Korea’s hunger for hard currency.
It could also suggest that if the same hackers are responsible, the objective this time around was to cause damage and sow chaos rather than collect ransoms. The $4 billion in damage could be far more important to the perpetrators than the $70,000 or less in ransom payments collected. That could also explain why the gang’s handling of ransom payments seems so diffident, almost like an afterthought.
One more disturbing theory to consider: the attack that swept the globe last weekend could be just a dry run for something much worse. It is possible WannaCry was a hastily cobbled-together test of what the stolen NSA worm technology can do, possibly succeeding far beyond the hackers’ imaginations because they thought more potential victims would have long ago patched the Microsoft Windows security vulnerability that allows WannaCry to spread so aggressively. The small test transactions detected on the hackers’ Bitcoin account could support the theory of a test run that was supposed to be fairly small but quickly got out of hand.
Along those lines, reports of even more dangerous WannaCry variants continue to trickle in. Reuters noted one such report from the Check Point Software Technologies, Ltd. cyber security firm on Monday, which was infecting a new computer roughly once per second before it was stopped.
As with WannaCry, the new variant was thwarted with a kill switch server – a website that tells the virus to stop reproducing, created as a safety valve to give the hackers a way to shut down their creation if they desired. The kill switch for this new variant was evidently different from the one discovered over the weekend, which greatly mitigated the damage from the initial WannaCry attack.
COMMENTS
Please let us know if you're having issues with commenting.